Information Security Management
-
Information Security Risk Management Architecture
As cyber threats become increasingly severe, to ensure the company’s information security, an information and communication security organization is established, with information security manager and personnel, and the general manager as the highest executive of the organization. The team is responsible for external information risk assessment and resource introduction assistance, information security system establishment, information security supervision and audit, and continuous strengthening of information security concepts.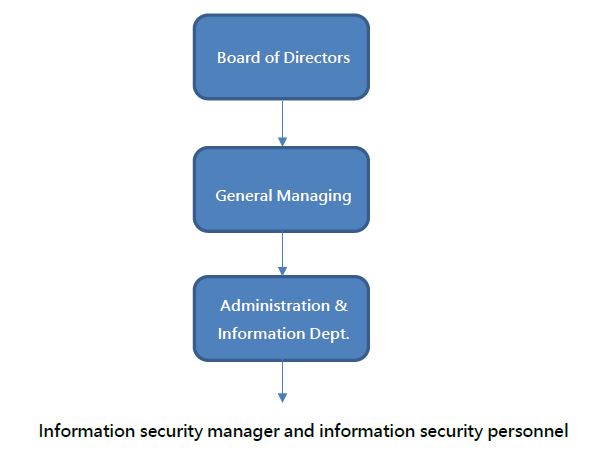
-
Information Security Policy
In order to protect the rights and interests of the company and employees, implement the company's internal information security, establish a reliable information security operating environment to ensure the confidentiality, integrity and availability of information assets, maintain the continuous operation principle of information systems, according to the planning, execution, audit and action (PDCA) management cycle mechanism, and hold regular meetings every month to review the applicability of information security policies.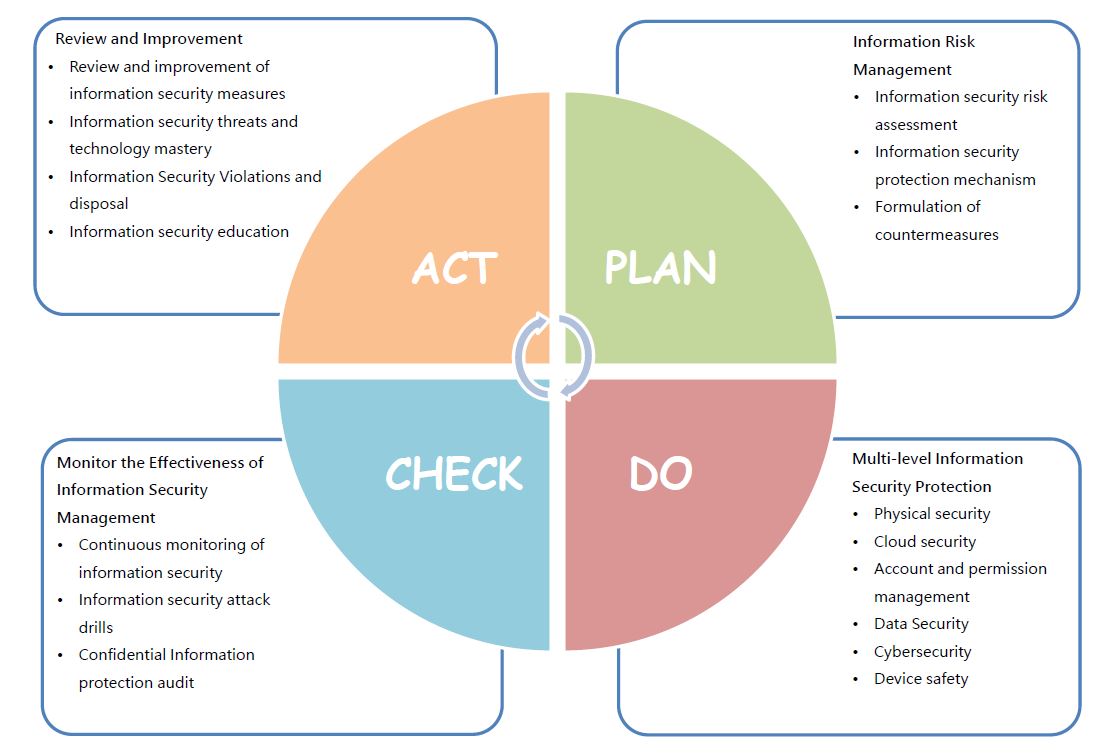
-
Specific Management Plan for Information Security
Project Operation Description Physical Security - Access control of the server room.
- The server room should be equipped with uninterruptible power supply (UPS) to ensure the stability of the circuit and the supply of power to the computer system for emergency use.
Cloud-Based Security - URL filtering to protect against malicious websites.
- Spam defense system
- Automatic email scanning threat protection, preventing unsafe attachments before users receive emails.
- Phishing emails, spam, and expanding protection scope of preventing malicious links.
Account and Permission Management - Change Passwords regularly and have a certain level of complexity.
- The account of the departing employee shall be deactivated immediately
Data Security - Perform off-site backup and restore drills.
- Implement a data loss prevention system.
Cybersecurity - Review firewall settings and connection rules to ensure blocking malicious attacks.
Device Safety - Install anti-virus software on endpoint devices.
- Automatically update the virus pattern.
-
Resources Invested in Information Security Management
To strengthen information security, irregularly conduct information security promotion with current events cases and information security cases reflected by employees during their daily work, and allocate appropriate budget every year to strengthen information technology and security protection, and hold a monthly information security meeting at the beginning of each month to regularly review the information security policy, and report the operation and execution results of information security to the board of directors regularly every year.
The control measures and operation status of the Company's information security in 2023 have been reported to the 3rd meeting of the 7th session of the Board of Directors on November 11, 2024.- A total of 5 information security promotions were conducted in 2024.
- Information security monthly meetings were held in 2024.
- New employee education and training completion rate 100%.
- Conducted email social engineering phishing email drill in 2024.
- No major information security incidents caused business damage in 2024.
- Completed information security education and training in 2024.
Investor Relations
E-mail:[email protected]
Tel: +886-3-563-5818
Address:No.6, Duxing 1st Rd., East Dist., Hsinchu City, Taiwan
Securities Agent
MasterLink Securities Corporation
Tel : +886-2-2768-6668
Fax : +886-2-2768-8778
Address:B1, No.35, Ln.11, Guangfu N.Rd., Songshan Dist., Taipei City, Taiwan
